Recently we were notified by a supplier that a particular application that we exposed via the NetScaler to Internet was vulnerable to particular exploit.
The only way to mitigate the threat was by making sure that only a specific path could be used, and nothing else.
For example: you only want that webmail.domain.com/owa works, and nothing else.
No problem! The NetScaler can fix that for you! This is how.
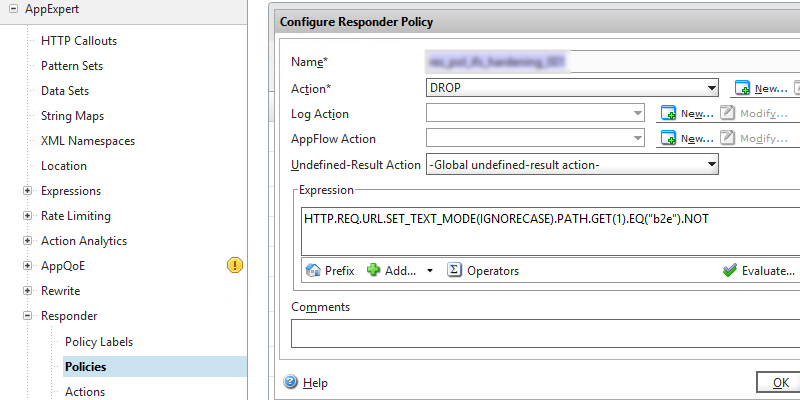
Create a responder policy and choose as action: DROP. Not NOOP (No Operation), you want to do something with it.
Expression will be:
HTTP.REQ.URL.PATH_AND_QUERY.CONTAINS("owa").NOT
The downside of doing it like that it is CASE sensitive. To overcome that, you can use this expression:
HTTP.REQ.URL.SET_TEXT_MODE(IGNORECASE).PATH.GET(1).EQ("owa").NOT
Or if you have like two paths that should work, and nothing else use it like this, in case that path1 OR path2 are matched:
HTTP.REQ.URL.SET_TEXT_MODE(IGNORECASE).PATH.GET(1).EQ("owa").NOT || HTTP.REQ.URL.SET_TEXT_MODE(IGNORECASE).PATH.GET(1).EQ("ecp").NOT
After this, just add is a responder policy to your vServer and test it out.
Cheers,
David
