UPDATE 17-aug-2017: Well Citrix did what they promised to do. The Citrix Netscaler nCore version 12 build 51.24 was released on 14th of July. In the release notes it is mentioned in the Fixed Issues section that issue #0654092 is resolved. But when I tested it, the issue was not resolved that I described earlier in this post. So I raised a ticket at Citrix TAC and explained and demonstrated everything. Also I tested it on a fresh out-of-the-box VPX v12 build 51.24; also same result.
After Citrix TAC consulted there Dev Team, Citrix has raised a new Enhancement request number, that is #0692815. Hopefully it will be resolved in the near future, but I can imagine that this has quite far-stretching consequences because it should be addressed outside of the NetScaler OS.
UPDATE 23-jun-2017: Citrix Support confirmed to me that CTX215496 will be addressed/fixed in version 12.0 build 51. This build is sheduled for release on 30th of June 2017 if everything go's to plan.
One of the first things that come to my mind when publishing a website towards the public internet is; SECURITY.
A good start is getting it on HTTPS; but once on HTTPS, you must make sure that the known weaknesses of securing SSL connections is properly dealt with.
To test this, I usually use the SSL Server Test of Qualys SSL Labs; a free online service that performs a deep analysis of the configuration of any SSL web server facing the public internet.
By making sure that the correct Cipher Suites are used in a correct order, weak SSL protocols (like SSLv3) are turned off and known exploits like POODLE and POODLE_TLS are mitigated, you are a on a good path.
How to accomplish this on a NetScaler (one of my favorite load balancers) is by taking care of these things. You can read about it here on this Citrix Blog article.
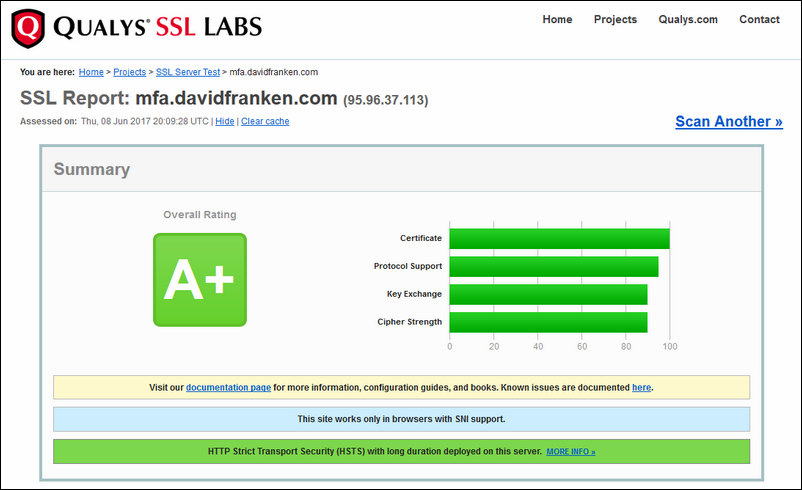
Once done, you may test it on Qualys SSL Labs. If correctly followed, you will get a A+ rating; see figure 1 below.
But sometimes, you will only see an A-rating (see figure 2). You probably checked everything and compared one to another, to come to the conclusion everything is set OK... but still getting only a grade A; how is this possible comes to mind (with a few swear words :) )
I had also to deal with this issue; I noticed that directly published public internet facing websites get a A+ grade, but when a AAA-TM form of the NetScaler gets involved it did got better than a A-rating.
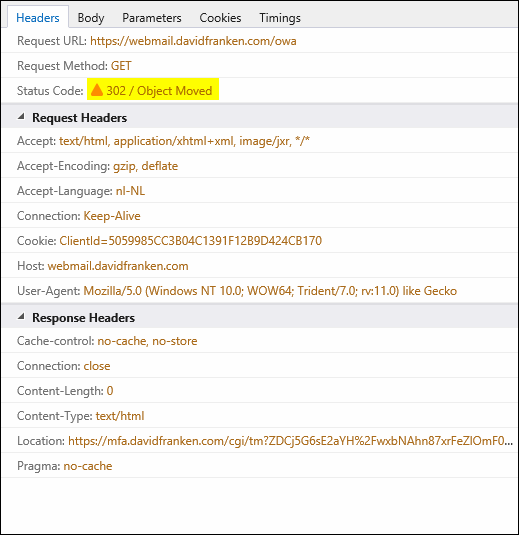
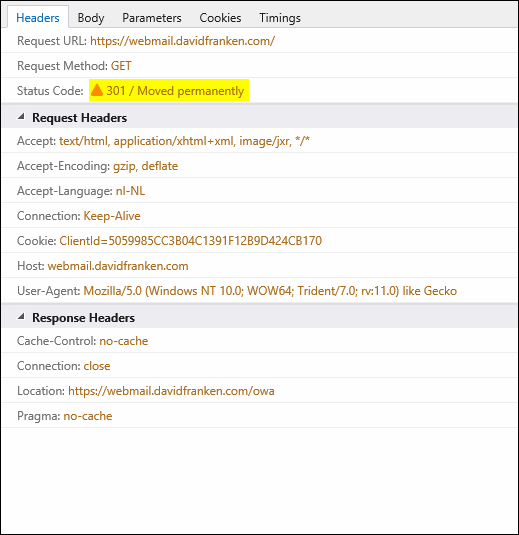
After looking closer to this, I noticed this only happens when a HTTP 302 of 301 is used (see figure 3).
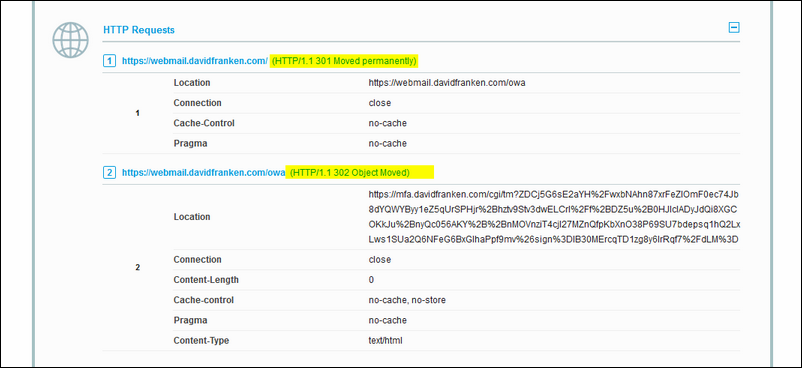
When you visit a website terminated on a virtual server on the NetScaler, and the VIP itself also depends on a Authentication Server; the NetScaler will throw in a HTTP 302 so that you can authenticate first, before you can continue.
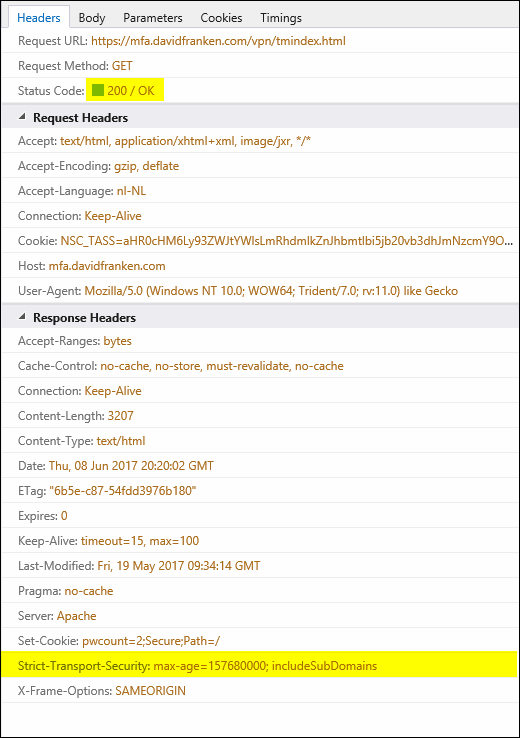
And here lies the problem. The NetScaler does not insert the Strict-Transport-Security value in the RESPONSE HEADER when it does a redirect via a HTTP 301 or 302 (see figure 4 and 5), only on a HTTP 200 (see figure 6). This is because the redirect takes place outside of the NetScaler, so the rewrite policy does not 'stick'. More on this issue here.
Hopefully Citrix will resolve this issue soon; the last time the Citrix edited the article was on 01 aug 2016; ; Citrix mentioned they put it on the Enhancement ticket for the Citrix Developers working on the NetScaler.
